How to – Use the full functionality of the ViciDial installer by carpenox
Vicidial administrators, take note: the Carpenox Auto Installer is about to change the game. This tool transforms the usually complex setup of Vicidial into a smooth, hassle-free experience. Let me go over some post installation steps and key things to take note of and changes I suggest you make after the fact of using the installer. I will give you a few steps to do first:
This assumes you have installed already through this article: How to – Install Vicidial on Alma Linux 9 with my new auto installer
Step 1 – Login to the admin GUI and change the default password
After you reboot the server, which should only be done once you have attached the FQDN(Fully Qualified Domain Name) for the SSL cert in the very last step of the installation process. This step is important and I advise you don’t skip it if you plan to use webphones that are built into the installer. If you do skip this step, make sure you turn the firewall off before trying to run it post the initial install or certbot wont be able to get through to create the SSL. The command is “service firewalld stop” and then start it back again after you install the SSL. This being said, then login to that domain in your browser. For example: https://my.dialer.one (Use your domain this is NOT real)
The default login is 6666 and password 1234 – make sure you change this password and then go into users and give yourself all the permissions possible.
If you do decide to not use webphones and can not or will not be installing SSL, you will need to login still through the https port with https://192.168.1.1 (your IP) and change the password the same. You will need need to add the http port to your trusted zone as well as the dynamic portal non SSL port to public which is 81. You can do so with the following commands:
firewall-cmd --permanent --add-port=81/tcp
firewall-cmd --add-service=http --zone=trusted --permanent
firewall-cmd --reloadStep 2 – Lock the firewall down
Hackers these days are quick, like I mean I have had servers provisioned from well known hosting companies like Hetzner, Vultr, DigitalOcean, OVH Cloud, IONOS, Contabo and many others within 15 minutes. They scan these known IP ranges and go for known vulnerabilities very quick and will install rootkits, crypto miners, DDOS bots and other malware. The firewall rules I have set in place leave the needed ports to be open to use the dialer in the “trusted” zone, however I have left port 443(https) open to public zone so you can login and change the default password, because you can not use the dynamic portal to validate your IP until after the default password has been changed.
So, now that you’ve changed that password, lets remove the https port 443 from the public zone. To do so type the following commands: You can also see more use for the firewall here: How to – Use Firewalld via command line
firewall-cmd --permanent --remove-service=https
firewall-cmd --reload
You also need to update the dynamic portal redirect link with this command:
nano /var/www/vhosts/dynportal/valid8.php
Change the https://cyburdial.com/agc/cyburdial.php to https://yourdomain.com/agc/vicidial.php

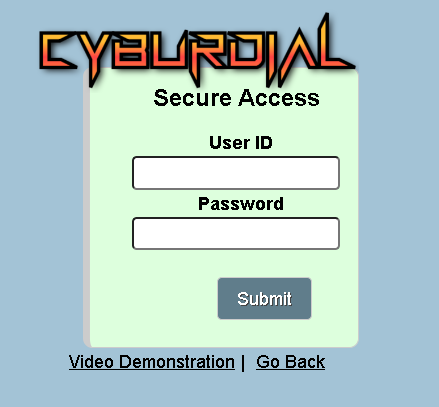
You should not be able to get to your domain at this point, you will need to use the dynamic portal login to validate your IP. You can find the URL for this at https://my.dialer.one:446/valid8.php (Again, use your domain) or for those of you that are only using IP – http://192.168.1.1:81/valid8.php. When you go to that page you will see a login area that looks like the image below:

If you have followed the previous steps you should now be redirected to the ViciDial agent page to login with your username and password. Just browse to the admin area by removing the /agc/vicidial.php part. Some more advanced steps would be to change the Dynamic portal port off of 446 to something above the 50000 range as it takes more time for hackers to scan this high and they typically will not waste the time. Changing the name of the valid8.php file is also a good standard operating procedure to put in place, however this take some other changes in the template file as well, that I will not go over on this article. If you would like to see an article for that, post a comment below.
Step 3 – Setup your ViciDial instance
At this point, most of you should know how to setup your your Vicidial configurations and setup. If not make sure to check out a few of my friends YouTube pages with lots of content regarding this:
- The GOAT of ViciDial and the Asterisk dialplan GOD Striker24x7: https://www.striker24x7.com/p/video-tutorials.html
- Harold aka HBTutorial at: https://www.youtube.com/@hbtutorial
- NewbieSolutions at: https://www.youtube.com/@NewbieSolutions
If you do decide to use the standard-db.sh file on my github, there is one thing that I messed up on the original design that needs to be fixed post import. Adding an “a” to the phone login on each user account. To run the standard-db file which comes pre-configured with everything ready to go other than adding DID’s and your VoIP carrier IP, simply run the commands below:
cd /usr/src/vicidial-install-scripts
chmod +x standard-db.sh
./standard-db.shOnce you use this file, your new password to get into the 6666 user will be “CyburDial2024”
After this go into each user account an add the letter “a” to the phone login area as shown below:

Step 4 – Add DID’s and Carrier IP
This next step is going on the thought of using the standard-db file on my github, but for those of you that do the config’s yourself, don’t forget the bulk tools area is a great way for adding your DID’s in bulk.

The next step is to add your DID’s, you can do so easily through the bulk tools in Admin > Reports > admin utilities
After this go Admin Bulk Tools
Click the highlighted area and the first area you see will be to copy DID’s, select the one I have there that says Copy this DID as shown below and paste your DID’s in the area available, then click submit.


Paste them in this box and click submit
The second part of this is to change the carrier IP in admin > carriers > carrier

That’s it, you can start dialing. Now lets go over a few tools I have added to help manage and debug your systems:
- sngrep – a command-line tool used for capturing and analyzing SIP (Session Initiation Protocol) packets
- htop – an interactive system monitor and process viewer for Unix system
- iftop – a similar tool used for the network card interface
- postfix – a free and open-source mail transfer agent (MTA) that routes and delivers email
- dovecot – an open-source IMAP and POP3 email server for Unix-like operating systems
- roundcubemail – a web based GUI for email
- inxi – detailed hardware information (inxi -Fxz)
Hopefully this helps with some of the questions I have been asked and common issues people run into. If you have any other questions, feel free to join my discord channel: https://discord.gg/ymGZJvF6hK or comment below.
Chris aka carpenox
Leave a Reply