How to – Secure Vicidial, correctly. Part 1
This article will show you how to secure Vicidial server correctly. This is definitely one of the topics, that I am asked about the most, so with that being said, this will be a multipart series with different “layers” of security from the basic way you need to secure your system in todays remote world, and as advanced as encrypted passwords, recordings, two factor authentication and more.

The steps I will cover in this article, will be the steps to take once you have finished installing a fresh Vicidial server. It will cover a single server setup, not a cluster which requires some additional steps to be shown later on in this series. This article will also presume you are setting this up for remote access, not just local. Let’s get started.
Secure Vicidial
Step 1 – Setup access through YAST firewall.
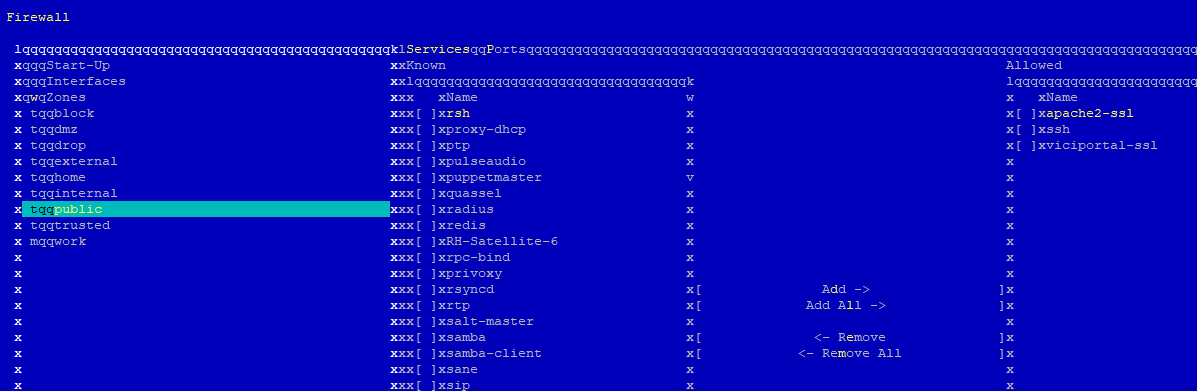
At the Linux CLI, type “yast firewall” and the following screen will pop up:

Go down to “Interfaces” and select your NIC card that has WAN access and change the zone from default to public:

Then TAB over to the public zone and remove all entries but apache2-ssl and ssh, then add viciportal-ssl.

Finally, add these services to your “Trusted” zone and TAB over to [Accept] and press enter.

This completes the first step for securing your Vicidial server’s firewall access.
Step 2 – Granting access for Dynamic portal & IP whitelist access only through the VB-firewall crontab entry
The next thing you need to do is change the crontab entry from blacklist being blocked to whitelist and dynamic access only. To do so, type “crontab -e” at your Linux CLI and you should see the following:

“Page down” until you see the VB-firewall entries near the bottom and change them as you see below:

Ok, so these steps above will prepare your server for the next steps of this process which I have written in other articles already, but I will link them here for easy navigation.
Step 3 – Enabling IP Whitelist
You can follow my blog post about IP whitelist, here.
Step 4 – Setting up the dynamic portal
You can follow the article for these instructions, here.
Well, that’s it for part 1, you have now setup your system for secure remote access to your server through IP whitelist & dynamic portal only. As always, feel free to comment below with any questions or issues you have along the way. My team and I are always available to help our Vicidial community secure themselves against the threats todays world comes with such as BazarCall malware, Ryuk and Conti Ransomwares and other cyber threats that directly target the telecommunications industry. Please protect yourself accordingly, if you need help with this, please fill out the form below for a FREE security audit or if you need some technical assistance on your servers.
Well, that’s it from us here at CyburDial for today, but please stay tuned for Part 2 of this series which will cover adding in other servers for a cluster type environment and how to allow access only to certain services on each server that are needed for communication between the cluster such as MySQL.
I hope this helps.
-Nox


David Blum
You should re-do the PuTTY images – “Use font encoding” on the “Translation” settings page will use the proper line-drawing characters regardless of the font you use for your terminal session (at least in my experience)…thanks!